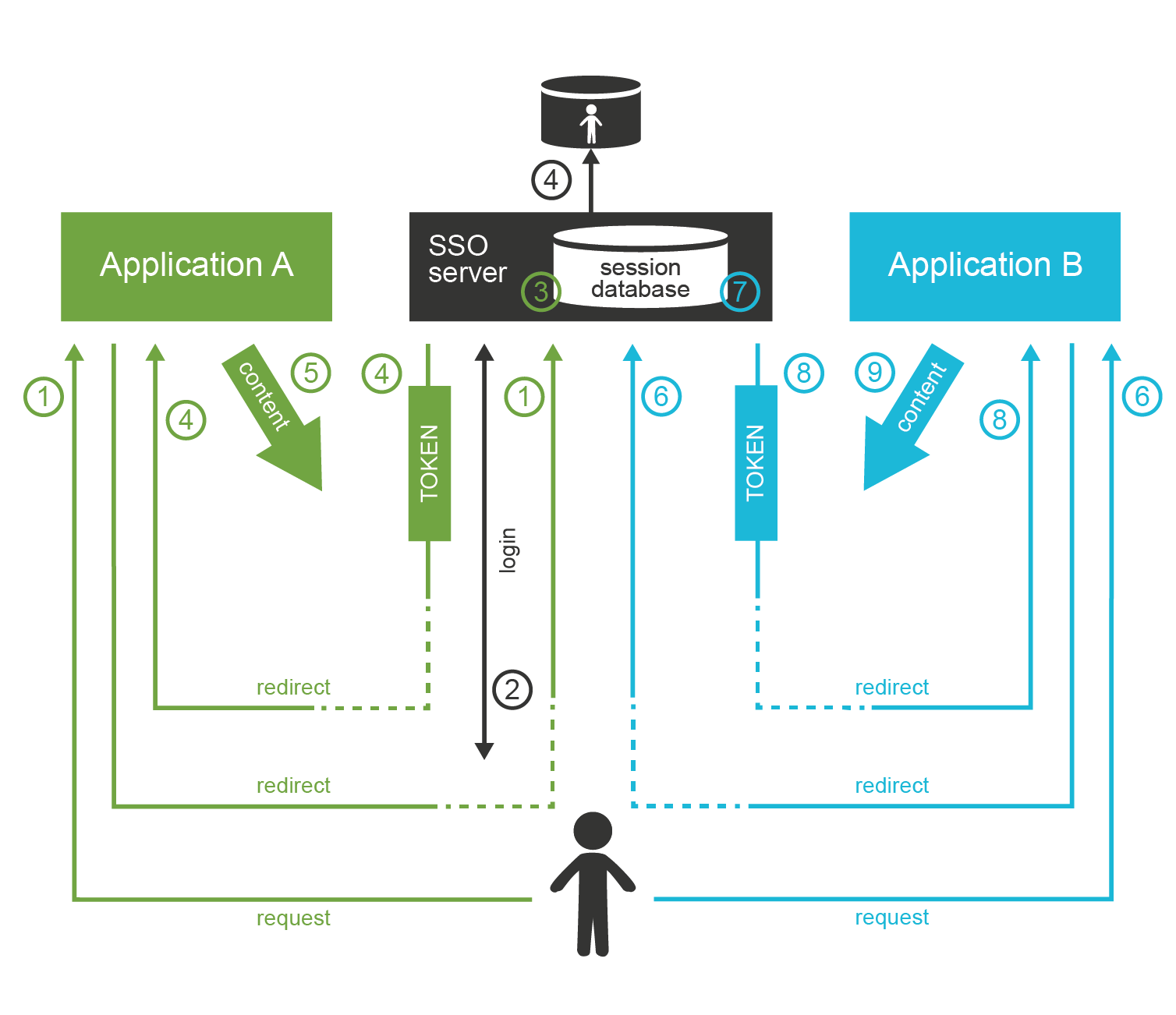
Forefront Identity Management – Certificate Management (FIM CM 2010) – Part 2 | Ammar Hasayen - Blog
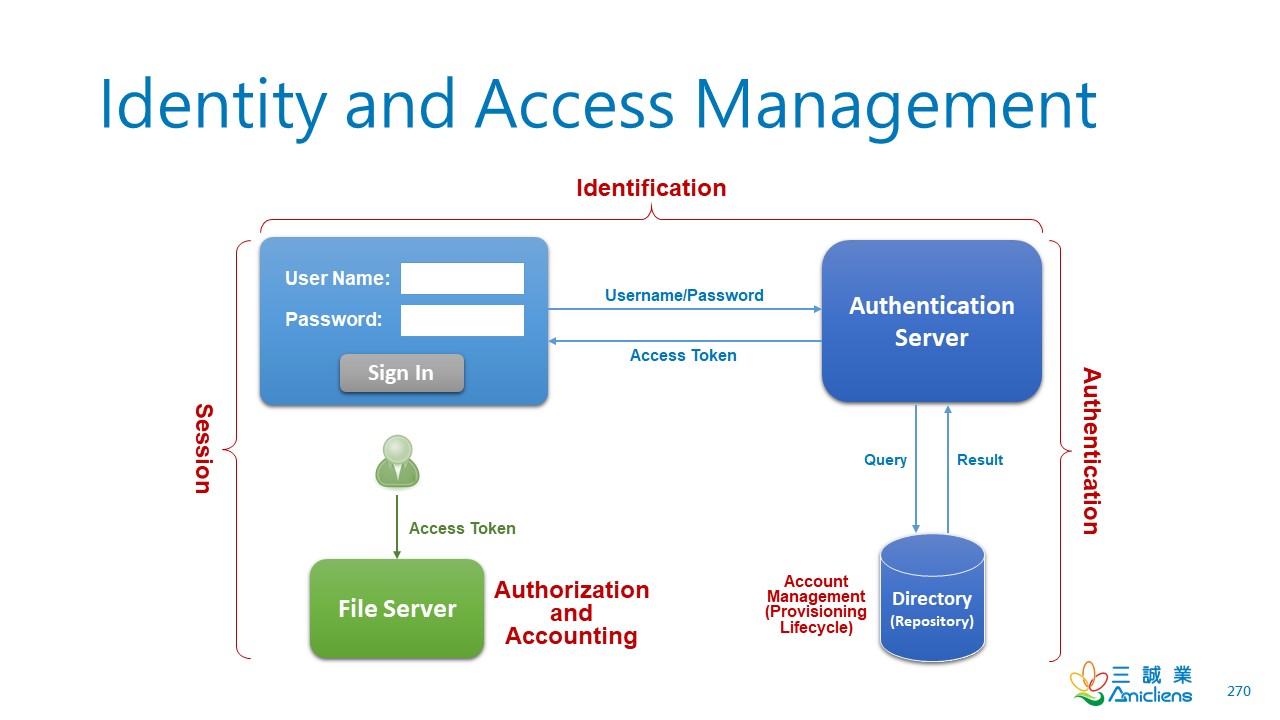
Identity and Access Management by Wentz Wu, CISSP/ISSMP/ISSAP/ISSEP,CCSP,CSSLP,CISM,PMP,CBAPWentz Wu
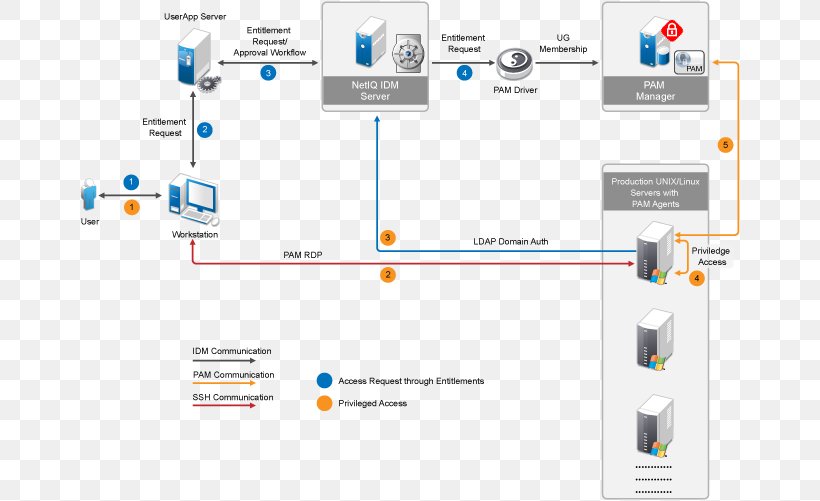
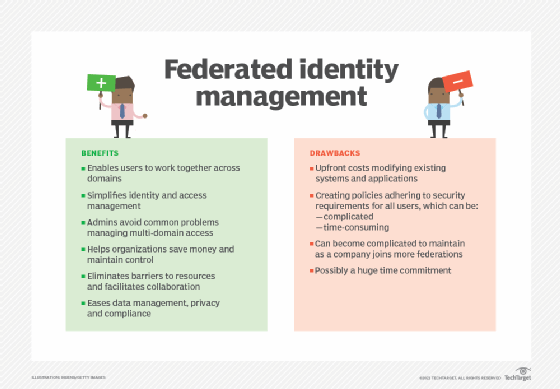
NetIQ Identity Manager Identity Management Technology Lightweight Directory Access Protocol, PNG, 661x501px, Netiq, Access Control, Brand,
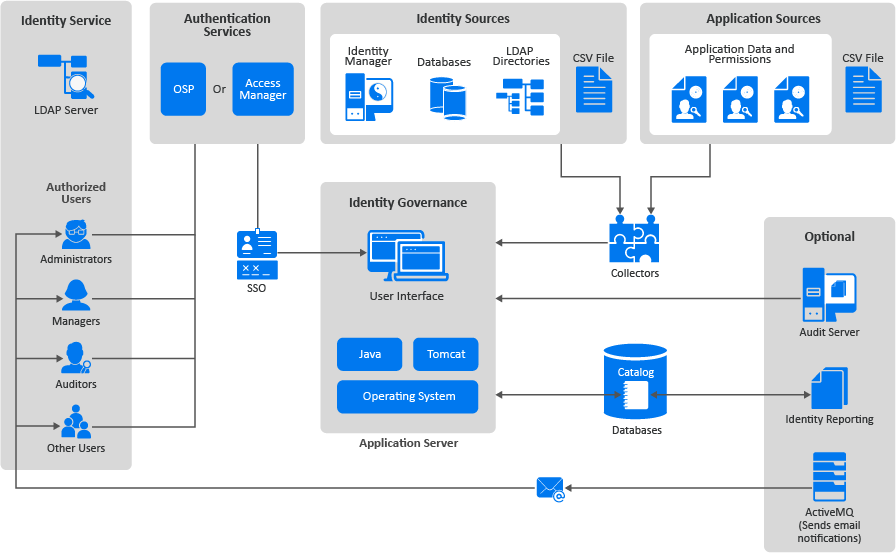
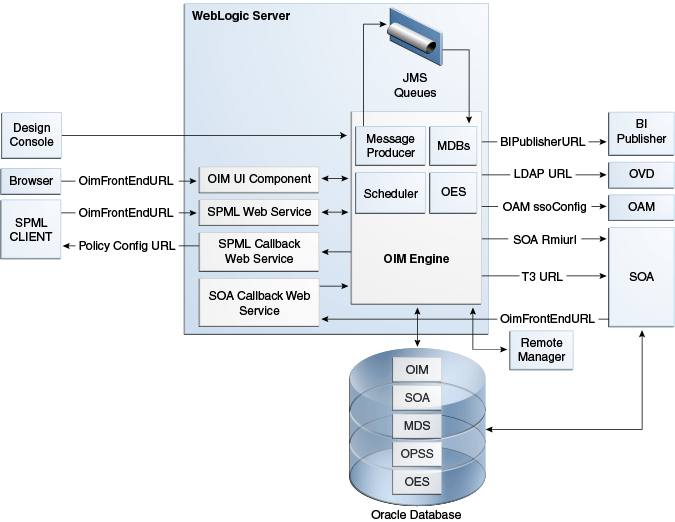
Understanding the Identity Governance Components - Identity Governance 3.6 Installation and Configuration Guide
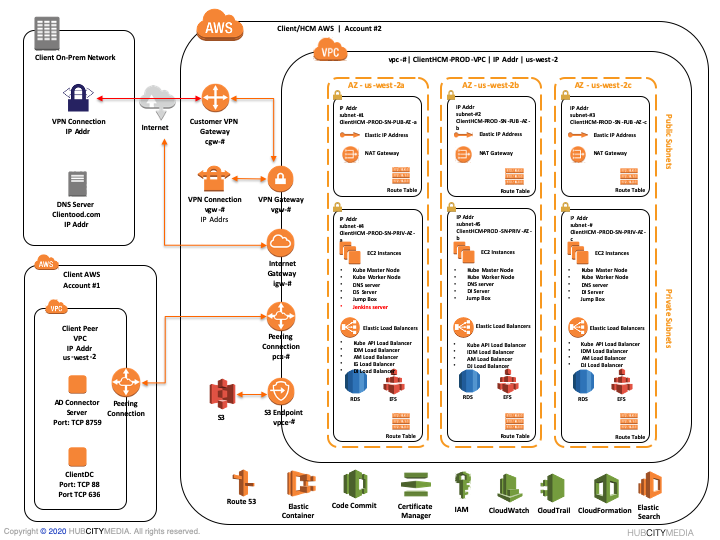




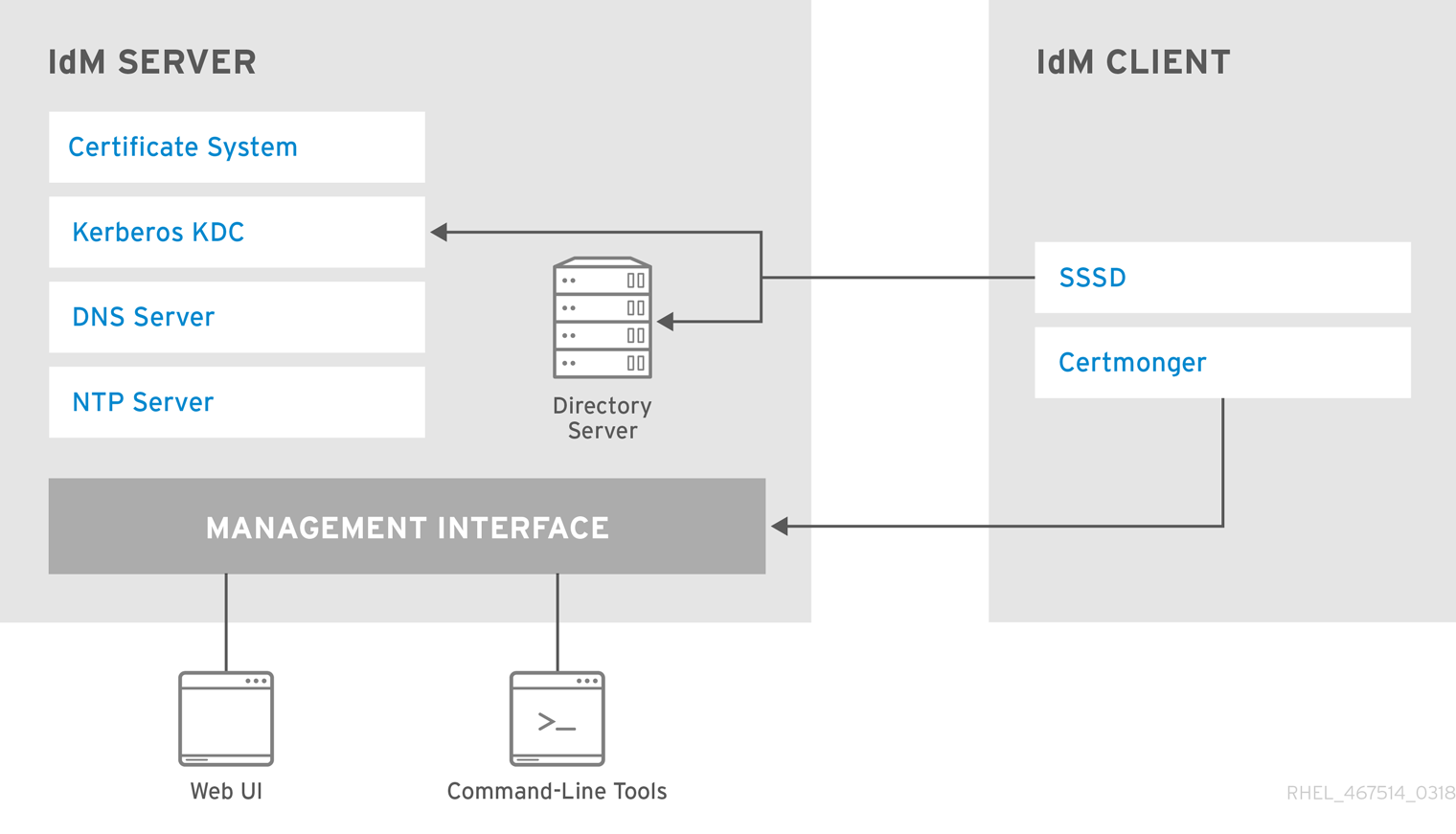

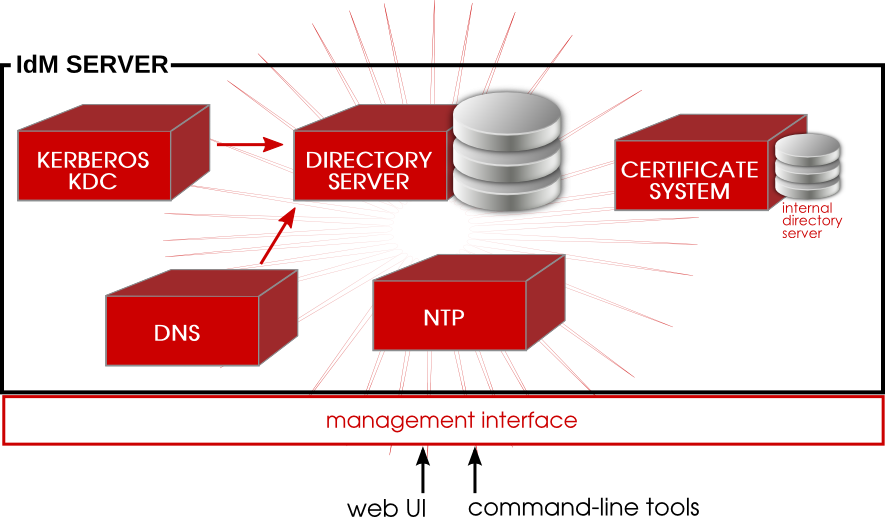
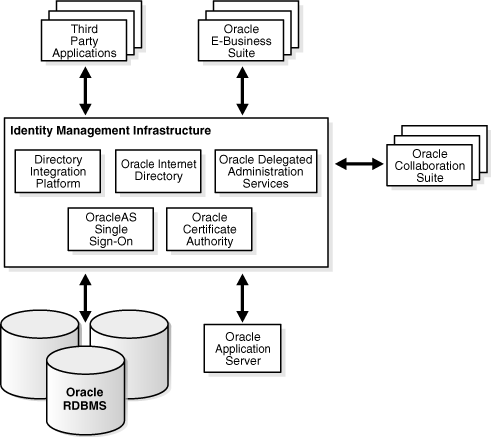

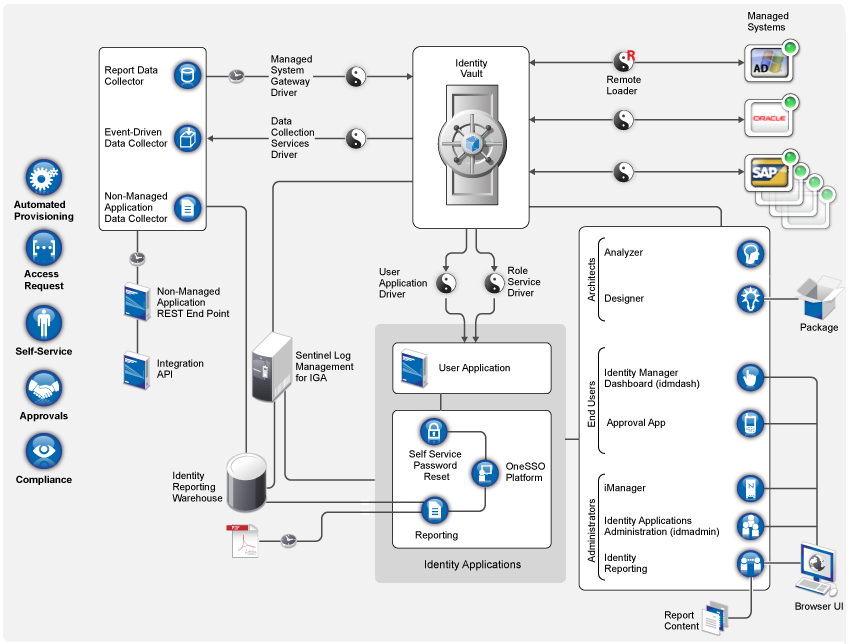
.jpeg)