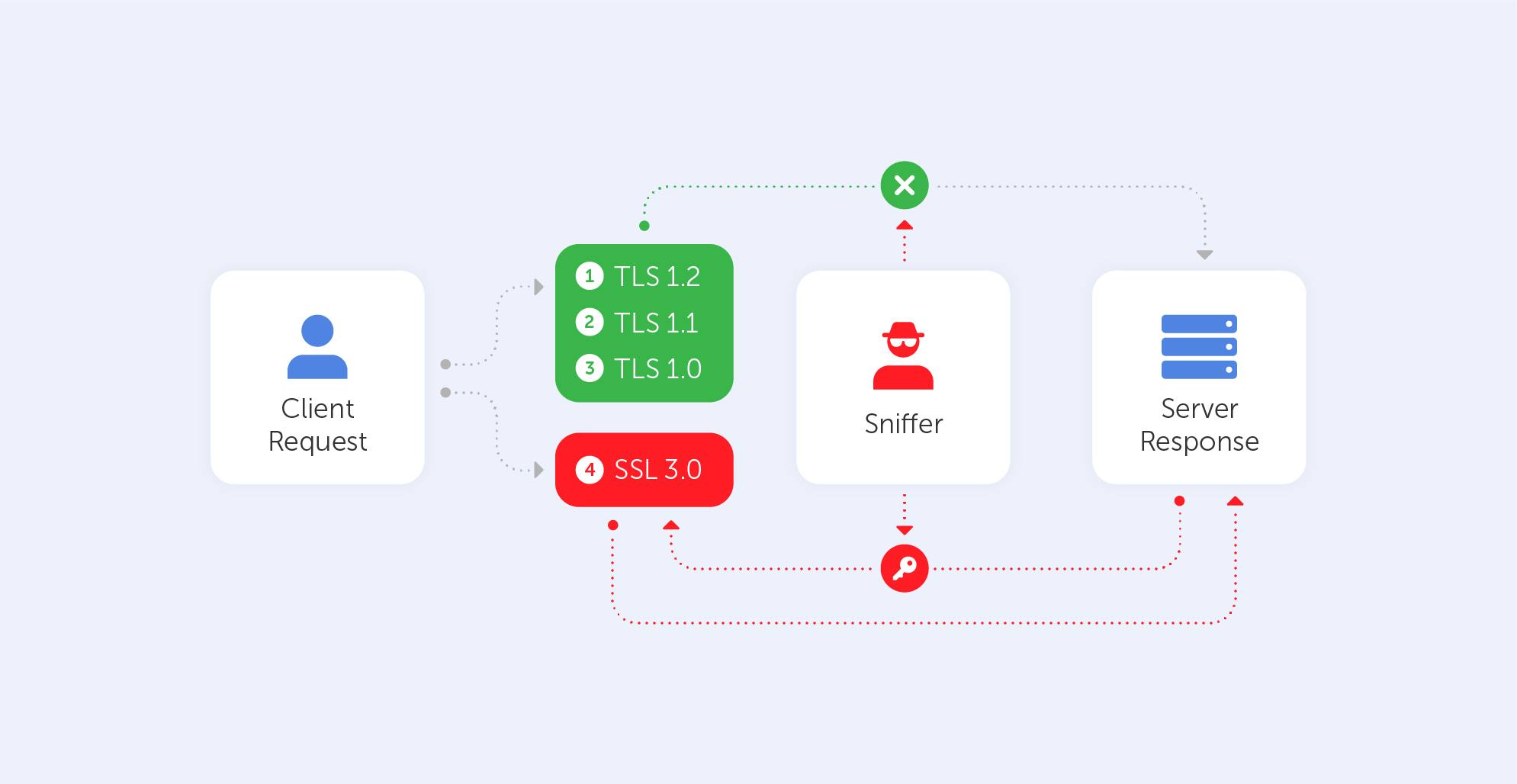
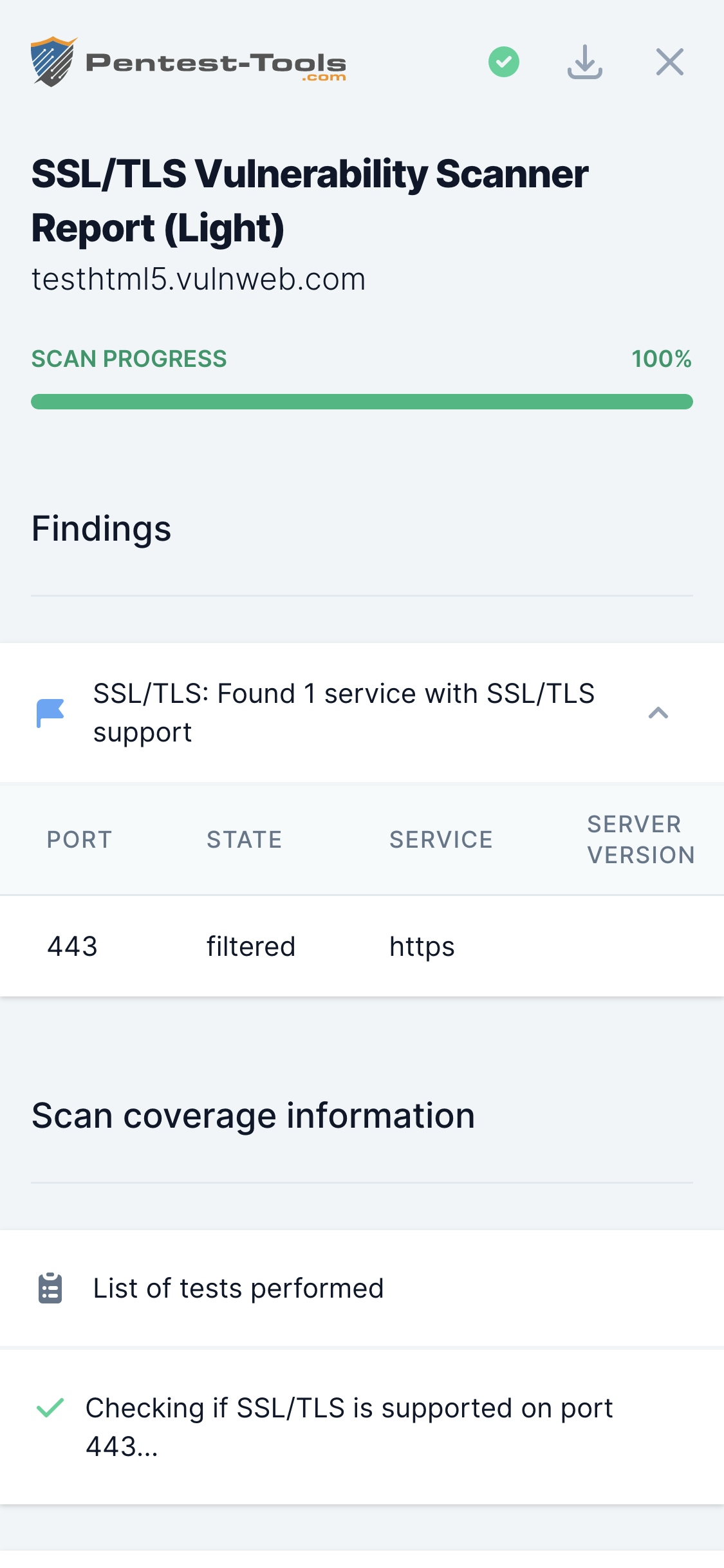
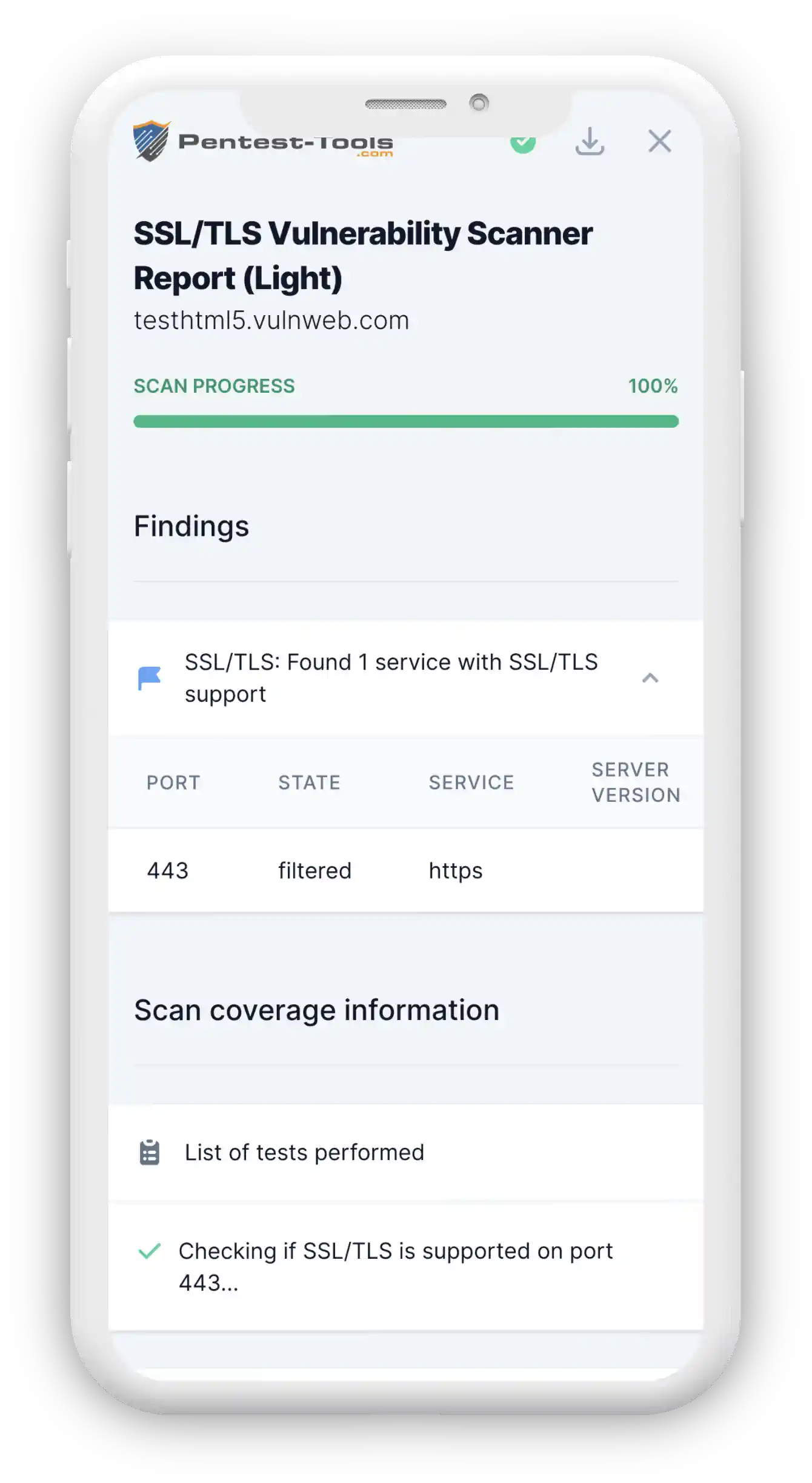
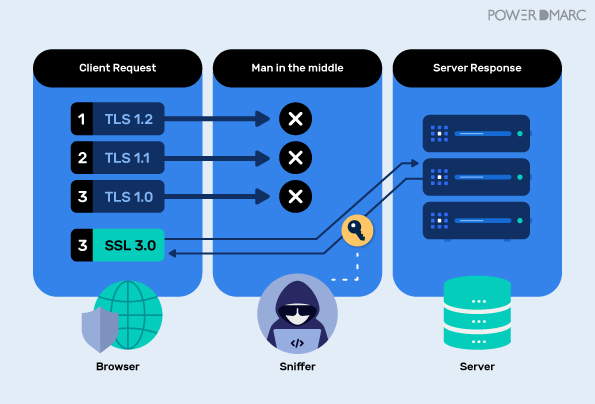
Story of a 2.5k Bounty — SSRF on Zimbra Led to Dump All Credentials in Clear Text | by Yasho | InfoSec Write-ups
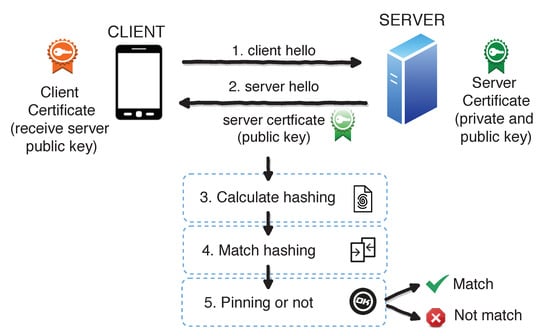
Entropy | Free Full-Text | A Framework to Secure the Development and Auditing of SSL Pinning in Mobile Applications: The Case of Android Devices